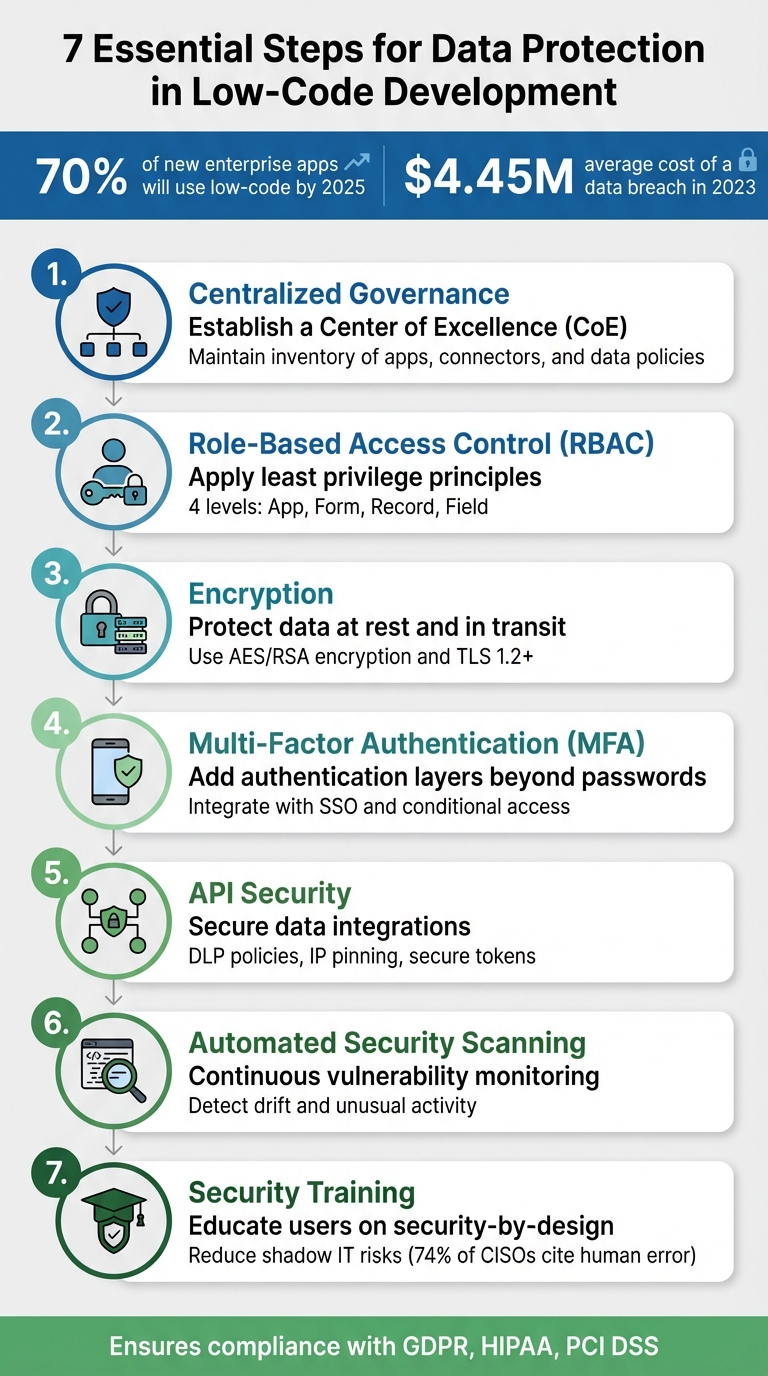
Low-code platforms let you build applications faster, but they also introduce unique security risks. By 2025, 70% of new enterprise apps will be developed using low-code tools, often by users without formal cybersecurity training. This can lead to issues like misconfigured permissions, unsecured APIs, and shadow IT. With the global average cost of a data breach reaching $4.45 million in 2023, protecting sensitive data is critical.
Here’s a quick overview of 7 key steps to secure low-code environments:
- Centralized Governance: Maintain control with a Center of Excellence to manage apps, connectors, and data policies.
- Role-Based Access Control (RBAC): Limit user access to only what’s necessary using least privilege principles.
- Encryption: Protect data at rest and in transit using AES or RSA encryption.
- Multi-Factor Authentication (MFA): Add extra layers of security beyond passwords.
- API Security: Secure integrations with strong authentication and data loss prevention policies.
- Automated Security Scanning: Continuously monitor for vulnerabilities and unusual activity.
- Training: Educate users on security best practices to reduce risks tied to shadow IT.
These measures not only protect sensitive data but also help ensure compliance with regulations like GDPR, HIPAA, and PCI DSS. While low-code platforms offer speed and flexibility, strong governance and security practices are essential to minimize risks.
7 Essential Steps for Data Protection in Low-Code Development
Why Low-code/No-code doesn't mean Low/No Security
sbb-itb-33eb356
1. Set Up Centralized Governance and a Low-Code Center of Excellence
A Center of Excellence (CoE) acts as the nerve center for maintaining low-code development platform security. It keeps an up-to-date inventory of all apps, automations, connectors, and data objects within your organization. This visibility allows security teams to identify issues like identity impersonation, data breaches, or excessive sharing before they escalate into serious problems. By establishing this centralized control, you create a foundation for stronger data protection strategies, which will come into play in later steps.
Modern governance tools prioritize efficiency by using automated guardrails while supporting low-code CX transformation initiatives rather than relying on manual checks. Platforms like Power Platform and Superblocks include built-in governance features to ensure compliance and maintain security. As the team at Superblocks advises:
"Governance shouldn't feel like a blocker, so don't let it become one".
Effectiveness in Protecting Sensitive Data
Strong governance immediately reduces risks in decentralized projects. By enforcing secure, pre-configured connectors instead of direct database connections, it minimizes the chances of data leakage. It also ensures that standardized security policies apply across all projects, so new applications automatically adopt organizational security settings and authentication protocols. This approach helps mitigate risks like misconfigured permissions and shadow IT. Additionally, early data classification using categories like Public, Internal, Confidential, and Highly Confidential helps prioritize security efforts in the areas that need it most.
Compatibility with Regulatory Compliance Requirements
Audit logging and change tracking are essential for meeting compliance requirements under frameworks like GDPR and HIPAA. Centralized governance ensures adherence to data residency rules, retention policies, and encryption standards. Typically, new data policies can be fully enforced across an organization within an hour, although in rare cases, it might take up to 24 hours.
Scalability for Enterprise-Level Applications
Automated monitoring and deployment controls make it easier for IT teams to manage a large number of decentralized apps. Tenant-level policies centralize management while scaling effortlessly across the organization. At the same time, environment-level policies allow for flexibility, accommodating specific needs of individual business units. By maintaining separate environments for development, testing, and production, organizations can prevent untested or insecure changes from affecting live systems.
2. Use Role-Based Access Control (RBAC) and Least Privilege Principles
To strengthen low-code data security, Role-Based Access Control (RBAC) works by limiting user access to only what’s necessary for their job. This means users are assigned roles like "Sales Representative", "Manager", or "Auditor", with permissions tailored specifically to their responsibilities. Instead of granting broad access, RBAC ensures users only see and interact with what they need. The least privilege principle takes this a step further by reducing permissions to the bare minimum required. Together, these practices align with centralized governance, ensuring that even authorized users are restricted to essential data and features.
Low-code platforms such as Power Platform apply RBAC across four levels: app-level (controlling who can access the app), form-level (deciding which screens users can view), record-level (managing which data rows users can interact with), and field-level (hiding or showing specific columns). For example, you can restrict access to sensitive details like social security numbers, while still allowing users to view and edit other fields in the same record.
Effectiveness in Protecting Sensitive Data
RBAC is a direct countermeasure to Broken Access Control, which OWASP identified as the top web security vulnerability in its 2021 Top 10 list. By following the least privilege approach, you limit the damage a compromised account can cause, as it won’t have access to unnecessary data or features. Many platforms adopt a "Default Deny" policy, requiring explicit permissions to access features, even if someone attempts to bypass user interface controls.
Ease of Implementation Within Low-Code Platforms
Beyond its theoretical benefits, implementing RBAC in low-code environments is straightforward. Most proprietary low code platforms offer pre-built security roles and templates that integrate seamlessly with centralized identity systems like Microsoft Entra ID. For example, you can assign roles to groups like "Accounting Team" or "Regional Managers" to simplify management. Features like Just-in-Time (JIT) access grant temporary privileges only when needed, while Just-Enough-Access (JEA) ensures users receive only the permissions required for specific tasks. To avoid security risks, avoid hardcoding credentials; instead, use tools like Azure Key Vault or environment variables.
Compatibility with Regulatory Compliance Requirements
RBAC aligns well with regulatory requirements by making security decisions transparent and easy to audit. Tools like Microsoft Purview help automate the discovery and classification of sensitive data, such as personally identifiable information (PII), aiding compliance with data protection laws. Regular access reviews ensure that permissions are updated when employees change roles or leave the organization. As LoginRadius explains:
"RBAC isn't just about allowing or denying entry. It's about controlling visibility down to individual records and sensitive fields. Without that depth, RBAC becomes a checkbox exercise rather than a real data security strategy".
Scalability for Enterprise-Level Applications
RBAC replaces inconsistent access decisions with a structured, role-based model that scales effectively as organizations grow. By assigning permissions through security groups, enterprises can efficiently manage thousands of users across multiple departments. However, as teams expand, organizations should watch for "role explosion" or privilege creep, where users accumulate unnecessary permissions over time. Regular audits help identify and correct these issues, ensuring access remains tightly controlled. When combined with centralized governance, RBAC provides a solid framework for managing access in enterprise environments.
3. Encrypt Data at Rest and in Transit
Encryption is a critical layer of security that protects data both when stored (at rest) and while being transmitted (in transit). By using algorithms like AES and RSA, encryption scrambles data, making it unreadable to unauthorized users. Application-Level Encryption (ALE) takes this further by encrypting data at its source, ensuring even database and cloud administrators are excluded from the trust boundary, reducing the risk of privilege abuse.
Effectiveness in Protecting Sensitive Data
Encryption tackles two key vulnerabilities: data stored in databases or on disks and data moving across networks. Data at rest encryption prevents unauthorized access or theft of stored information, while data in transit encryption protects communication between systems using protocols like TLS 1.2 or higher. For instance, platforms like Microsoft Power Platform automatically block any HTTP traffic using outdated TLS versions, such as 1.1.
Gautam Zalpuri, IBM's CTO for Data & Security, highlights the value of ALE:
"Application-level encryption (ALE) provides an additional layer of protection by encrypting data at its source. ALE can enhance your data security, privacy and sovereignty posture".
These encryption methods integrate seamlessly into low-code environments, bolstering their security capabilities.
Ease of Implementation Within Low-Code Platforms
Low-code platforms simplify encryption by offering intuitive settings and free low-code platforms often include these as core features. Developers can activate encryption for local databases through simple toggles or use "no-code" brokers that apply encryption without altering the application's backend logic. Leading platforms also provide Transparent Data Encryption (TDE) and Azure Storage Encryption by default, using provider-managed keys.
For mobile applications with offline functionality, ensure local databases and files are encrypted to safeguard device-stored data. Cryptographic keys should be stored securely in tools like Azure Key Vault. Additionally, all communication between clients and external services should use secure TLS connections, avoiding fallback to less secure protocols.
Compatibility with Regulatory Compliance Requirements
Encryption is a cornerstone of compliance with regulations like GDPR, HIPAA, and PCI DSS. Low-code platforms support these standards by offering tools to meet legal requirements. For highly regulated environments, customer-managed keys (CMK) stored in secure vaults allow organizations to rotate or revoke access as needed. Implementing HTTP Strict Transport Security (HSTS) ensures web communications remain on HTTPS, while automating SSL/TLS certificate renewal prevents lapses in secure communication.
Scalability for Enterprise-Level Applications
Encryption methods like symmetric encryption (AES) are efficient and capable of handling large data volumes, making them ideal for enterprise applications. Modern encryption brokers maintain high performance while scaling to meet growing demands. For international operations, low-code platforms support multi-geo deployments, allowing data to be stored in specific regions to meet local regulations. Tools like service tags simplify managing network access controls for encrypted traffic, while regular purging of temporary or sensitive data reduces potential vulnerabilities.
4. Enable Multi-Factor Authentication (MFA) and Secure Authentication Methods
After implementing strong encryption, adding Multi-Factor Authentication (MFA) creates an additional layer of security. MFA works by verifying user identities through multiple steps before granting access to sensitive systems and data. With the rising costs of data breaches, using MFA has become critical for safeguarding financial transactions, personal health records, and customer information from cyberattacks.
Effectiveness in Protecting Sensitive Data
MFA significantly reduces the chances of unauthorized access by requiring more than just a password, addressing risks like stolen credentials or misconfigured permissions. As Team Kissflow security experts put it:
"Adding layers of authentication minimizes the risk of unauthorized access to critical systems".
This approach mitigates key security threats highlighted by OWASP, such as Account Impersonation (CD-SEC-02) and Authentication Failures (CD-SEC-05). By pairing MFA with conditional access policies, organizations can enforce authentication based on specific factors like user location or the sensitivity of the data being accessed. This layered security model integrates seamlessly with modern low-code tools.
Ease of Implementation Within Low-Code Platforms
Low-code platforms make integrating MFA straightforward, often including it as a built-in feature that leverages centralized identity systems. For example, platforms like Microsoft Entra ID combine Single Sign-On (SSO) with MFA to streamline secure access. Instead of juggling multiple passwords, users authenticate once using enterprise-managed credentials. Meanwhile, managed connectors handle OAuth flows and API key management in the background , following a low-code security checklist for integrations, ensuring that citizen developers don’t have direct access to sensitive authentication details.
Compatibility with Regulatory Compliance Requirements
MFA also helps organizations meet the access control requirements of major regulatory frameworks like GDPR, HIPAA, and CCPA. It aligns with federal security mandates, incorporating guidance from agencies such as NIST, CISA, and the OMB. Secure authentication practices ensure organizations maintain audit-ready logs for compliance purposes. As Microsoft’s security documentation highlights:
"Proper management of secrets is crucial for maintaining the security and integrity of your application, workload, and associated data. Improper handling of secrets can lead to data breaches, service disruption, regulatory violations, and other issues".
Scalability for Enterprise-Level Applications
MFA’s benefits extend to enterprise-scale applications, ensuring consistent security as organizations grow. Centralized authentication systems can support thousands of users while maintaining uniform security protocols. With projections indicating that 60% of software development organizations will adopt low-code platforms as their primary development method by 2028, scalable authentication is becoming increasingly important. Modern platforms enforce strict security standards, such as requiring TLS 1.2 or higher for all HTTP traffic, automatically rejecting outdated and vulnerable protocols. This centralized model ensures MFA and other authentication measures are applied consistently across the entire application ecosystem, regardless of size.
5. Apply API Security and Secure Data Integration Practices
In low-code environments, ensuring strong API security is essential for protecting your data. APIs act as the bridge between low-code apps and external systems, making them a primary target for attackers. By combining robust authentication with secure API integration, you can safeguard data as it flows across systems.
Effectiveness in Protecting Sensitive Data
Secure API practices play a key role in preventing data breaches by regulating how information moves between systems. For example, Data Loss Prevention (DLP) policies can block risky connectors or restrict certain operations, like permitting "Read" access while blocking "Delete" actions. Network-level security measures, such as IP pinning, ensure that only requests from authorized IP addresses can interact with workflows or access integration endpoints. For HTTP-based integrations, requiring Microsoft Entra ID tokens adds an extra layer of user authentication. Additionally, enabling features like "Secure Inputs" and "Secure Outputs" ensures that sensitive data, such as passwords, is not exposed in run histories or audit logs.
Ease of Implementation Within Low-Code Platforms
Low-code platforms simplify API security by offering built-in features. Instead of embedding API keys or passwords directly into workflows, developers can use environment variables connected to Azure Key Vault to securely retrieve secrets during execution. Managed connectors streamline processes by handling OAuth, API key management, and token refreshes automatically, reducing the risk of human error. Granular action-level filtering allows developers to control exactly what data can be sent or received through each connector. To further enhance security, administrators can implement API rate limiting to prevent abuse and manage API quotas effectively. Testing integrations in sandbox environments with synthetic data is another critical step for identifying vulnerabilities before moving to production.
Compatibility with Regulatory Compliance Requirements
API governance is crucial for meeting stringent compliance requirements like GDPR and HIPAA. Detailed audit logs track every instance of data access and exchange, ensuring transparency. Enforcing encryption protocols like TLS 1.2 or higher safeguards Personally Identifiable Information (PII) and Protected Health Information (PHI) during transmission. For organizations subject to data residency rules, low-code platforms allow you to specify geographic regions for data storage, addressing GDPR concerns about cross-border data transfers. Azure Key Vault serves as a centralized tool for managing credentials securely, aiding in compliance audits. Automated tools like "Solution Checker" can analyze low-code solutions for insecure API patterns, helping to identify and resolve issues before deployment.
Scalability for Enterprise-Level Applications
Enterprise applications demand scalable and secure solutions. A hybrid architecture can help by keeping sensitive credentials within the corporate network while allowing cloud-based management. Designing data planes to initiate only outbound connections minimizes the external attack surface. Policy-as-Code approaches translate regulatory requirements into enforceable rules within CI/CD pipelines, ensuring that security measures grow alongside development. Administrators can further control data flow by categorizing connectors as "Business", "Non-Business", or "Blocked", preventing unauthorized interactions between sensitive APIs and public services. While policy changes in large enterprises may take up to 24 hours to fully propagate, most updates are enforced within an hour.
6. Run Automated Security Scanning and Regular Vulnerability Assessments
Effectiveness in Protecting Sensitive Data
Automated security scanning takes risk management to the next level by catching vulnerabilities that manual reviews often miss. These tools excel at spotting common issues like weak authentication, poor authorization practices, and insecure storage of sensitive data. They also monitor for "drift", where security measures weaken over time. Continuous monitoring can identify unusual activity, such as unexpected login attempts or spikes in data access, allowing for quick action before a breach occurs. Addressing these vulnerabilities early can save organizations from costly security incidents.
"Low-code apps belong in your pen-testing scope as soon as they touch real data or critical systems. Skipping them is like locking the front door and leaving the side gate open with a welcome mat."
- David Balaban, Cybersecurity Analyst
Ease of Implementation Within Low-Code Platforms
Low-code platforms make integrating automated security checks straightforward by embedding them directly into the development process. These platforms can be configured to block deployments if they detect missing encryption, excessive permissions, or insecure connections. Automated build gates ensure that apps without multi-factor authentication or encrypted data channels don’t make it to production. Other built-in features, like audit logging and anomaly detection, minimize the need for manual setup. This automation helps address the challenge of keeping up with rapid development speeds, reducing the risk of "shadow apps" slipping through unnoticed. By streamlining security and compliance tasks, these tools allow developers to focus on building while keeping workflows secure.
Compatibility with Regulatory Compliance Requirements
Regular vulnerability assessments play a key role in meeting compliance standards. Features like automated audit logs and security checkpoints help organizations adhere to regulations such as GDPR, PCI DSS, HIPAA, and SOX. For those working within frameworks like ISO 27001, SOC 2, or FedRAMP, continuous monitoring aligns with their stringent requirements. With predictions showing that by 2028, 60% of software development organizations will rely on low-code platforms as their main approach, automated compliance tools are becoming essential for staying ahead of regulatory demands.
Scalability for Enterprise-Level Applications
As organizations scale their use of low-code platforms, maintaining robust security across thousands of applications becomes critical. Centralized security dashboards provide the visibility needed to oversee large-scale deployments. Automated scanning adapts seamlessly to rapid app rollouts, ensuring IT teams maintain control even as new apps are introduced across various business units. Including low-code apps in penetration testing is vital when sensitive data is involved. While automated scans continuously catch known vulnerabilities, penetration testing uncovers deeper risks, such as logic flaws and vulnerabilities in third-party integrations. This dual approach ensures enterprise applications remain secure as they grow.
7. Train Developers and Business Users on Security-by-Design
Training is a powerful way to ensure that both developers and business users can integrate security-by-design into low-code development. Combined with automated controls and governance, this approach strengthens the overall security framework.
Effectiveness in Protecting Sensitive Data
Training plays a key role in reducing shadow IT by promoting centralized oversight of how data is handled. With proper education, users can implement encryption, data classification, and retention protocols right from the start. Developers trained on the OWASP Low-Code/No-Code Top 10 can spot vulnerabilities early in the process. This is essential, given that 74% of CISOs identify human error as their top security concern. Alarmingly, nearly half of all cyberattacks are linked to shadow IT.
"A low-code app builder without security training risk data exposure."
- Ben Wong, Senior Principal Technical Product Manager, Blackbaud
Ease of Implementation Within Low-Code Platforms
Low-code platforms simplify security by providing built-in tools like multi-factor authentication, role-based access control, and automated audit logs - all accessible without coding. Developers can use sandboxes with synthetic data to configure security controls safely. Pre-built security templates also make it easier to follow best practices. Platform-specific training highlights how to leverage these features effectively, showing users the immediate advantages of built-in security controls.
"Security has to be easy. If your security controls are so complex that people route around them, you've already lost. The goal is to make secure development the path of least resistance."
- Team Kissflow
This practical approach ensures that security becomes an integral part of the development process, rather than an afterthought.
Compatibility with Regulatory Compliance Requirements
Training complements encryption and access controls by teaching users how to create workflows that comply with regulations like GDPR, HIPAA, and CCPA. Pre-configured compliance modules in many platforms simplify this process. Training on the shared responsibility model clarifies that while the platform provider handles infrastructure security, users are responsible for securing application-level logic. Additionally, education on data classification and retention helps prevent sensitive information from being stored in plain text or kept longer than legally allowed. This also mitigates risks associated with "zombie apps" - unmonitored applications that retain access to production data and pose compliance risks.
Scalability for Enterprise-Level Applications
For large organizations, training aligned with centralized governance and technical controls ensures security can scale effectively. A Security Champions program is particularly useful, as it allows technically skilled individuals within business units to act as first-line resources, reducing the burden on IT teams. Instead of functioning as gatekeepers, security teams can use review processes to coach developers and enhance their expertise. Establishing risk thresholds for reviews and continuously updating training materials as new low-code features are introduced ensures the program remains effective over time.
Comparison Table
Industries adjust their data protection strategies based on regulations and the type of sensitive information they handle. For instance, healthcare providers must protect Protected Health Information (PHI), while financial institutions focus on securing cardholder and bank account data. Retailers prioritize safeguarding customer Personally Identifiable Information (PII), and government agencies adhere to strict data residency requirements. These tailored measures are especially important for low-code applications, where rapid development must not compromise security.
The table below highlights how different industries implement security measures to align with sector-specific compliance and risk management needs. For example, secure data transmission using TLS 1.2 or higher is a baseline practice. However, high-compliance sectors like healthcare and finance often use Customer-Managed Keys (CMK) for encrypting data at rest, while retail environments typically depend on Microsoft-managed keys. In low-code development, these adjustments complement encryption, RBAC, MFA, and other security strategies discussed earlier.
| Industry | Security Measure | Implementation Method | Industry-Specific Considerations |
|---|---|---|---|
| Healthcare | Encryption & MFA | Use Customer-Managed Keys (CMK) for encryption and enforce multi-factor authentication (MFA) via authenticator apps, hardware tokens (e.g., YubiKey), or biometrics. | Fully protect PHI, avoid SMS-based OTPs due to SIM-swapping risks, and comply with HIPAA, GDPR, and CCPA regulations [43, 12]. |
| Finance | RBAC & Access Control | Apply least privilege principles with clearly defined roles (e.g., User, Admin, Auditor) and use Microsoft Entra ID for fine-grained API access. | Meet PCI DSS standards by safeguarding cardholder and bank account data. Implement field-level security to reduce risks like account impersonation [21, 2]. |
| Retail | API Security & Data Leakage Prevention | Use sensitivity labels, ensure sanitized data synchronization between CRM and marketing tools, and restrict the use of custom connectors. | Protect customer PII during automated workflows and prevent unauthorized access caused by misconfigured integrations [2, 8]. |
| Government | Data Residency & Compliance | Deploy sovereign cloud solutions with regional data storage and utilize Customer-Managed Keys (CMK). | Ensure data stays within designated Azure geographies (Home Geo) and secure certifications like FedRAMP or IL5 to meet stringent security compliance requirements [35, 8]. |
For effective implementation, use your organization's data classification framework, store sensitive credentials like API keys and OAuth tokens in secure systems such as Azure Key Vault, and ensure sensitive data is purged from logs. These practices reinforce the earlier recommendations for safeguarding credentials in low-code environments.
Conclusion
Low-code platforms can speed up application development by as much as 5×, but with that speed comes the need for strong data protection measures. As Brian Fleming, Co-founder of Planet Crust, aptly puts it:
"Low code doesn't necessarily mean low risk."
To address these risks, the strategies discussed here - centralized governance, RBAC (Role-Based Access Control), encryption, multi-factor authentication (MFA), API security, automated scanning, and security-by-design training - create a multi-layered defense for low-code development. Together, these measures help safeguard your organization against financial losses, regulatory fines, and reputational harm, all while empowering citizen developers to create applications securely. It's important to remember that while low-code platforms often include built-in security features, internal governance is critical to prevent issues like shadow IT and zombie apps.
These practices not only protect sensitive data but also provide a framework for choosing the right platform. Before starting your next project, check out the Low Code Platforms Directory to explore platforms that comply with standards like ISO 27001, HIPAA, and GDPR. Look for features such as end-to-end encryption, single sign-on, and centralized governance to ensure your applications are secure from the start.
FAQs
What should we secure first in a low-code app?
Protecting data should be your number one priority when it comes to securing a low-code app. To keep things safe, make sure to implement access controls to restrict who can view or modify sensitive information. Use encryption to shield data both in transit and at rest, ensuring it stays secure even if intercepted. It's also crucial to identify and address any vulnerabilities right from the start of development. By doing this, you can minimize risks like unauthorized access or data leaks before they become a problem.
How can we prevent shadow IT and zombie apps?
To tackle shadow IT and prevent the rise of zombie apps in low-code environments, it's crucial to set up robust governance frameworks. These frameworks should outline clear approval processes, enforce security standards, and include ongoing app usage monitoring.
Take advantage of platform features like access controls, encryption, and activity logs to maintain oversight. Additionally, conduct regular audits to identify outdated or unused apps. Removing these not only ensures compliance but also minimizes potential risks.
By doing so, you can align citizen development efforts with your organization's security and compliance objectives, creating a safer and more efficient environment.
When should we use customer-managed encryption keys?
Customer-managed encryption keys give you complete control over your encryption process. You decide the protection level, where the keys are stored, how often they’re rotated, who can access them, and their overall lifecycle. This method strengthens security and makes it easier to track and audit sensitive data, helping you meet both organizational standards and regulatory demands.


